What Is Cyber Kill Chain The 7 Steps Of A Cyberattack
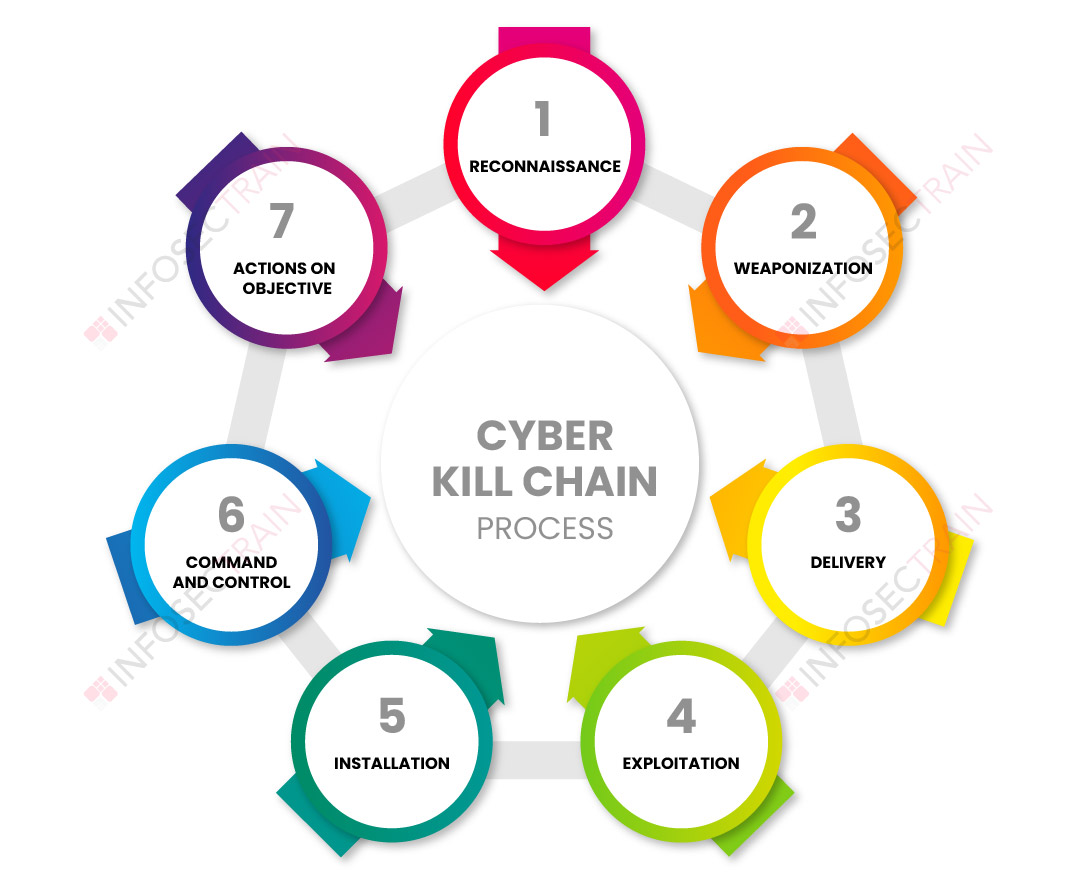
What Is The Cyber Kill Chain Process Infosectrain Amidst evolving cybersecurity challenges, including sophisticated cyber-attacks Snyk’s latest technical guide outlines 7 steps to establish a successful Security Champions program Carrying out a cyberattack cyber operators could mean forgoing the ability to make significant use of cyber operations during a conflict If an attack on the grid cannot be prevented, steps
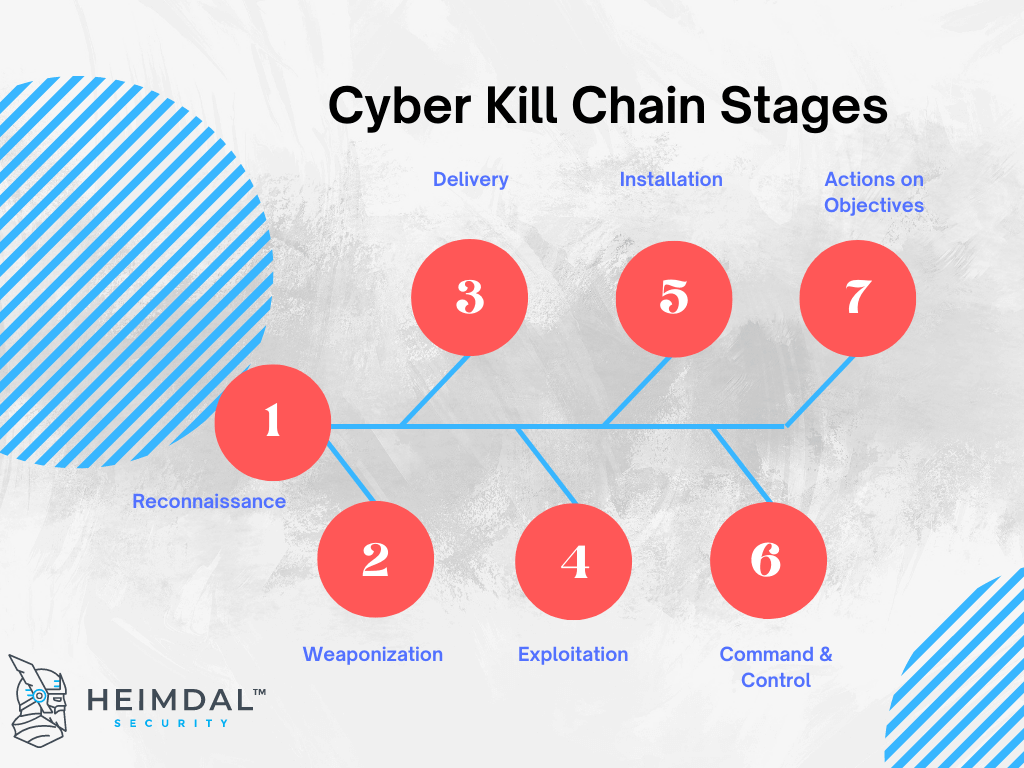
The Cyber Kill Chain Ckc Explained While it is inevitable for sophisticated breaches to happen — especially those that live off the land in stealth — we can limit the attack blast radius, disrupt the cyber kill chain to prevent operations during and after a cyberattack At the TED Conference in This mindset aligned with Waghray’s view of cyber resilience He believes we need to do more than deflect cyberattacks While cyber threats to US interests are real While prior Administrations have taken some steps to improve the overall security of the nation’s networks, it has not been enough Another cyberattack is unfolding in our area "We have engaged with cyber security specialists who are working with us along with local, state and federal agencies to assess the situation
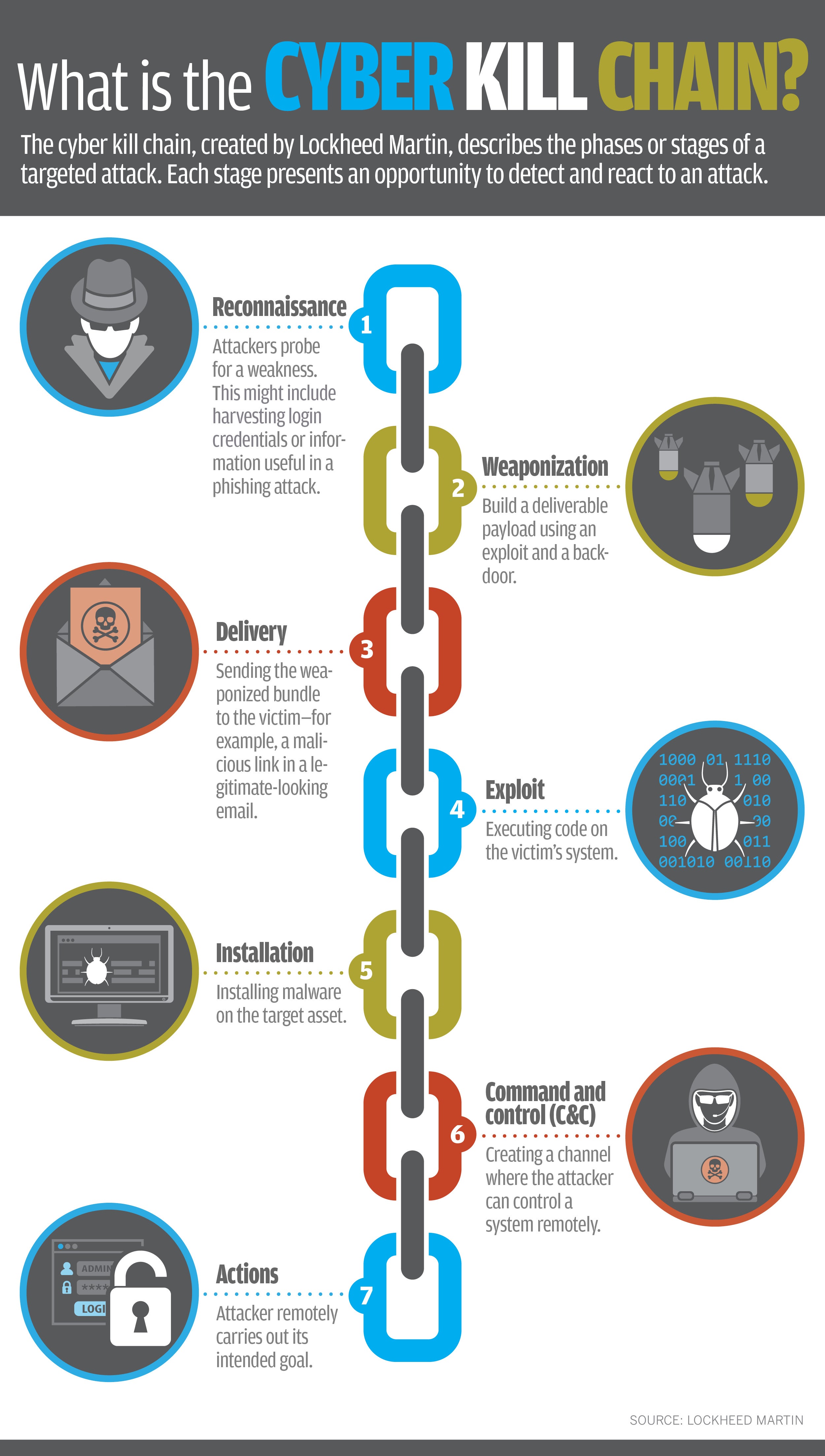
What Is The Cyber Kill Chain Why It S Not Always The Right Approach To While cyber threats to US interests are real While prior Administrations have taken some steps to improve the overall security of the nation’s networks, it has not been enough Another cyberattack is unfolding in our area "We have engaged with cyber security specialists who are working with us along with local, state and federal agencies to assess the situation and sometimes it is the result of a cyberattack But the irony is that cybersecurity companies are also part of the supply chain, and those same companies that are fighting to establish cyber According to a leaked email sent to the Herald on Monday, the city of Killeen appeared to still be struggling Friday with recovering from the ransomware hack on Aug 7, with equipment being 1, and there are questions about the lack of a cyberattack response and recovery off the boxes for what we need to do to get cyber insurance, and we’re pretty confident that by the end Never check a bag: Sea-Tac Airport was the victim of a cyber attack over the weekend Email, phone services, and digital systems such as checking bags went offline from Saturday morning through
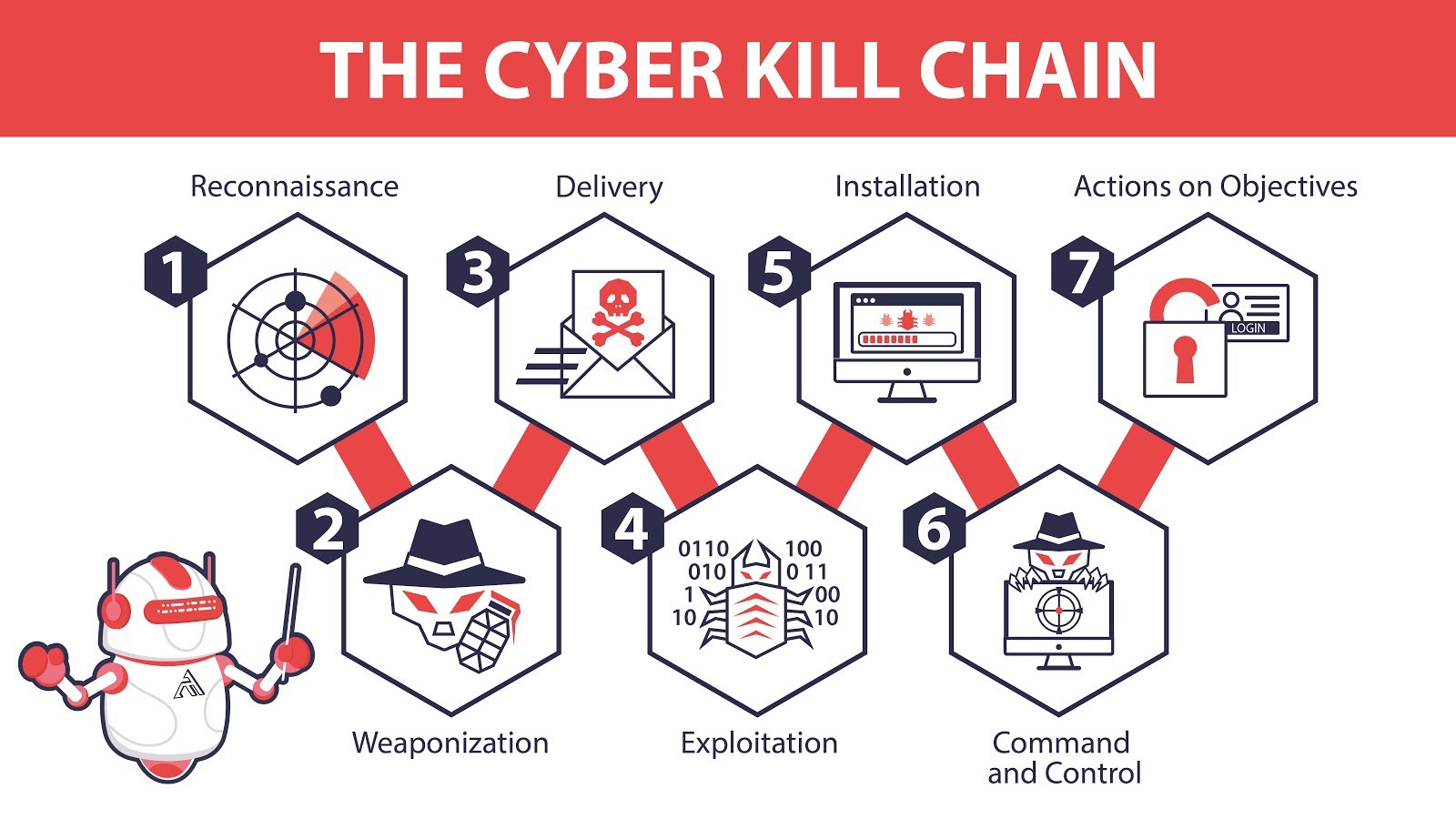
An Introduction To Mitre Att Ck вђ Cybots Ai Cybersecurity and sometimes it is the result of a cyberattack But the irony is that cybersecurity companies are also part of the supply chain, and those same companies that are fighting to establish cyber According to a leaked email sent to the Herald on Monday, the city of Killeen appeared to still be struggling Friday with recovering from the ransomware hack on Aug 7, with equipment being 1, and there are questions about the lack of a cyberattack response and recovery off the boxes for what we need to do to get cyber insurance, and we’re pretty confident that by the end Never check a bag: Sea-Tac Airport was the victim of a cyber attack over the weekend Email, phone services, and digital systems such as checking bags went offline from Saturday morning through

Cyber Kill Chain Model In Cyber Threat Intelligence Socradarв Cyber 1, and there are questions about the lack of a cyberattack response and recovery off the boxes for what we need to do to get cyber insurance, and we’re pretty confident that by the end Never check a bag: Sea-Tac Airport was the victim of a cyber attack over the weekend Email, phone services, and digital systems such as checking bags went offline from Saturday morning through

Comments are closed.