Steps For Cfos To Implement Zero Trust Cybersecurity Wsj

Steps For Cfos To Implement Zero Trust Cybersecurity Wsj Zero trust takes a new approach to cybersecurity, one that restricts network access for all users, applies security controls that hide applications not required by a particular user, and authenticates and continuously validates identities before allowing them to connect to the applications they need. it represents a clear break from traditional. Far from contained, the modern technology ecosphere can look dangerously ubiquitous. cfos can calculate the potential costs of not investing in zero trust. the average cost of a data breach has reached $4.24 million, an increase of nearly 10% over last year, according to a recent study. 1 in instances where higher levels of remote work were a.

How To Implement A Zero Trust Security Model F5 Vrogue Co A useful first step is to consider using a zero trust maturity model to determine the current state of the company’s defenses. cybersecurity efforts have traditionally focused on controlling the perimeters of an organization, but such an approach can be outdated given that interconnections among employees, customers, suppliers, and partners. The biden administration last week released a draft blueprint for a so called “zero trust” approach to fending off cyber hackers. here are the basics of of what it would look like in practice. Tools and techniques for architecting a zero trust network steps for cfos to implement zero trust cybersecurity. next generation firewalls (ngfw): devices that provide advanced traffic inspection and filtering capabilities. identity aware proxies: solutions that enforce access policies based on user identities and contextual factors. 1. define the attack surface. defining your attack surface should be the first item on your zero trust checklist. to do this, you want to hone in on the areas you need to protect. this way, you will not be overwhelmed with implementing policies and deploying tools across your entire network.

Steps Cfos Can Take To Add Value To It Wsj Tools and techniques for architecting a zero trust network steps for cfos to implement zero trust cybersecurity. next generation firewalls (ngfw): devices that provide advanced traffic inspection and filtering capabilities. identity aware proxies: solutions that enforce access policies based on user identities and contextual factors. 1. define the attack surface. defining your attack surface should be the first item on your zero trust checklist. to do this, you want to hone in on the areas you need to protect. this way, you will not be overwhelmed with implementing policies and deploying tools across your entire network. A zero trust architecture (zta) focuses on protecting data and resources. it enables secure authorized access to enterprise resources that are distributed across on premises and multiple cloud environments, while enabling a hybrid workforce and partners to access resources from anywhere, at any time, from any device in support of the organization’s mission. each access request is evaluated. Steps to implement zero trust in your business. identify sensitive data and assets start by identifying where your critical data resides and the digital assets requiring the highest protection levels. understanding what needs to be protected is crucial for effectively applying the zero trust principles. map the transaction flows.
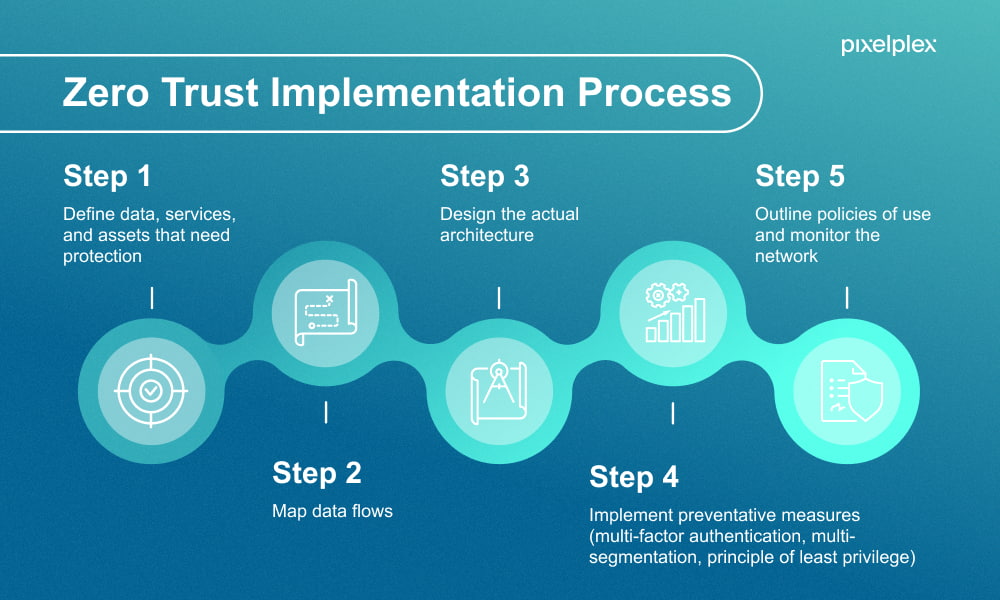
How To Implement Zero Trust Architecture In 5 Steps Checklist A zero trust architecture (zta) focuses on protecting data and resources. it enables secure authorized access to enterprise resources that are distributed across on premises and multiple cloud environments, while enabling a hybrid workforce and partners to access resources from anywhere, at any time, from any device in support of the organization’s mission. each access request is evaluated. Steps to implement zero trust in your business. identify sensitive data and assets start by identifying where your critical data resides and the digital assets requiring the highest protection levels. understanding what needs to be protected is crucial for effectively applying the zero trust principles. map the transaction flows.

The Comprehensive Guide To Zero Trust Architecture

Comments are closed.