Security By Design Strategies Building Unbreakable Software

Security By Design Strategies Building Unbreakable Software Youtube Welcome to our comprehensive guide on integrating robust security measures within the software development life cycle (sdlc), featuring mr.soumen mukherjee,. Secure by design is an approach to software development that prioritizes security as a core business requirement rather than a technical feature or afterthought. taking this approach, tech providers build security into the design process as well as every other stage of a product’s development lifecycle in order to identify and mitigate.

Security By Design O Que г E Como Comeг Ar Guia Completo We believe that a secure by design approach applied to developer ecosystems is one of the most effective ways to achieve high assurance levels of safety and security. a developer ecosystem designed for safety and security ensures security invariants for applications, and prevents entire classes of vulnerabilities, providing assurance at scale. October 25, 2023. cybersecurity best practices. cisa and 17 u.s. and international partners published an update to the joint secure by design product, “shifting the balance of cybersecurity risk: principles and approaches for secure by design software,” that includes expanded principles, guidance, and eight new international agency co sealers. Aws security by design framework. while the aws security by design framework is focused on aws workloads, its principles can be applied to any cloud or noncloud workload, regardless of platform. the framework includes four main steps: understand the requirements of the organization, outline its policies and map them against the controls. These principles are inspired by the owasp development guide and are a set of desirable properties, behavior, design and implementation practices that we take into consideration when threat modeling at red hat. principle: defense in depth. principle: secure by default. principle: least privilege. principle: separation of duties.
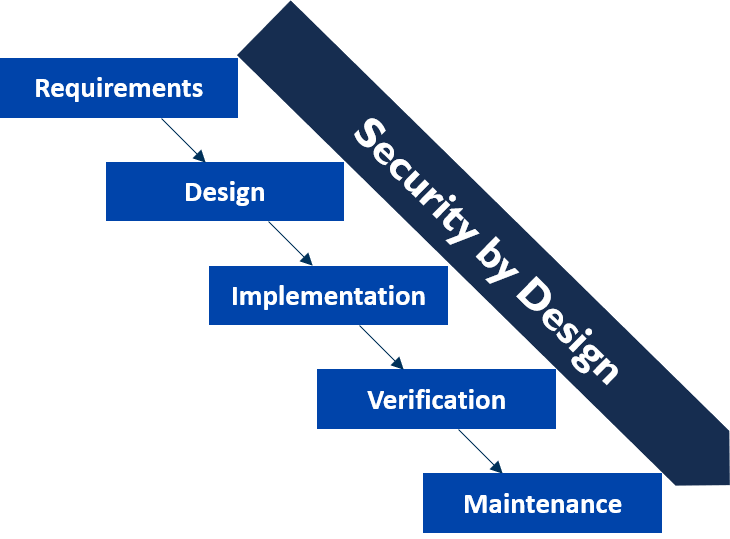
Cetome Security By Design Devsecops For Iot Aws security by design framework. while the aws security by design framework is focused on aws workloads, its principles can be applied to any cloud or noncloud workload, regardless of platform. the framework includes four main steps: understand the requirements of the organization, outline its policies and map them against the controls. These principles are inspired by the owasp development guide and are a set of desirable properties, behavior, design and implementation practices that we take into consideration when threat modeling at red hat. principle: defense in depth. principle: secure by default. principle: least privilege. principle: separation of duties. This way, if something is missed in design, it can be caught in development. devops teams should apply the following security by design principles into the sdlc: address possible abuse cases (e.g., how users may misuse the software). create and enforce secure code guidelines. use appropriate security tools. For brumley, secure by default means designing in security that works with how people use the software. "there are design principles that span multiple principles — just like when building a.
Security By Design Security Practices Throughout The Whole Software This way, if something is missed in design, it can be caught in development. devops teams should apply the following security by design principles into the sdlc: address possible abuse cases (e.g., how users may misuse the software). create and enforce secure code guidelines. use appropriate security tools. For brumley, secure by default means designing in security that works with how people use the software. "there are design principles that span multiple principles — just like when building a.

Comments are closed.