Phishing Attack Diagram

The Major Types Of Phishing Attacks How To Identify Them The This common email phishing attack is popularized by the “nigerian prince” email, where an alleged nigerian prince in a desperate situation offers to give the victim a large sum of money for a small fee upfront. unsurprisingly, when the fee is paid, no large sum of money ever arrives. the interesting history is that this type of scam has. Example of email phishing. hackers used linkedin to grab contact information from employees at sony and targeted them with an email phishing campaign. they got away with over 100 terabytes of data. 4. https phishing. an https phishing attack is carried out by sending the victim an email with a link to a fake website.
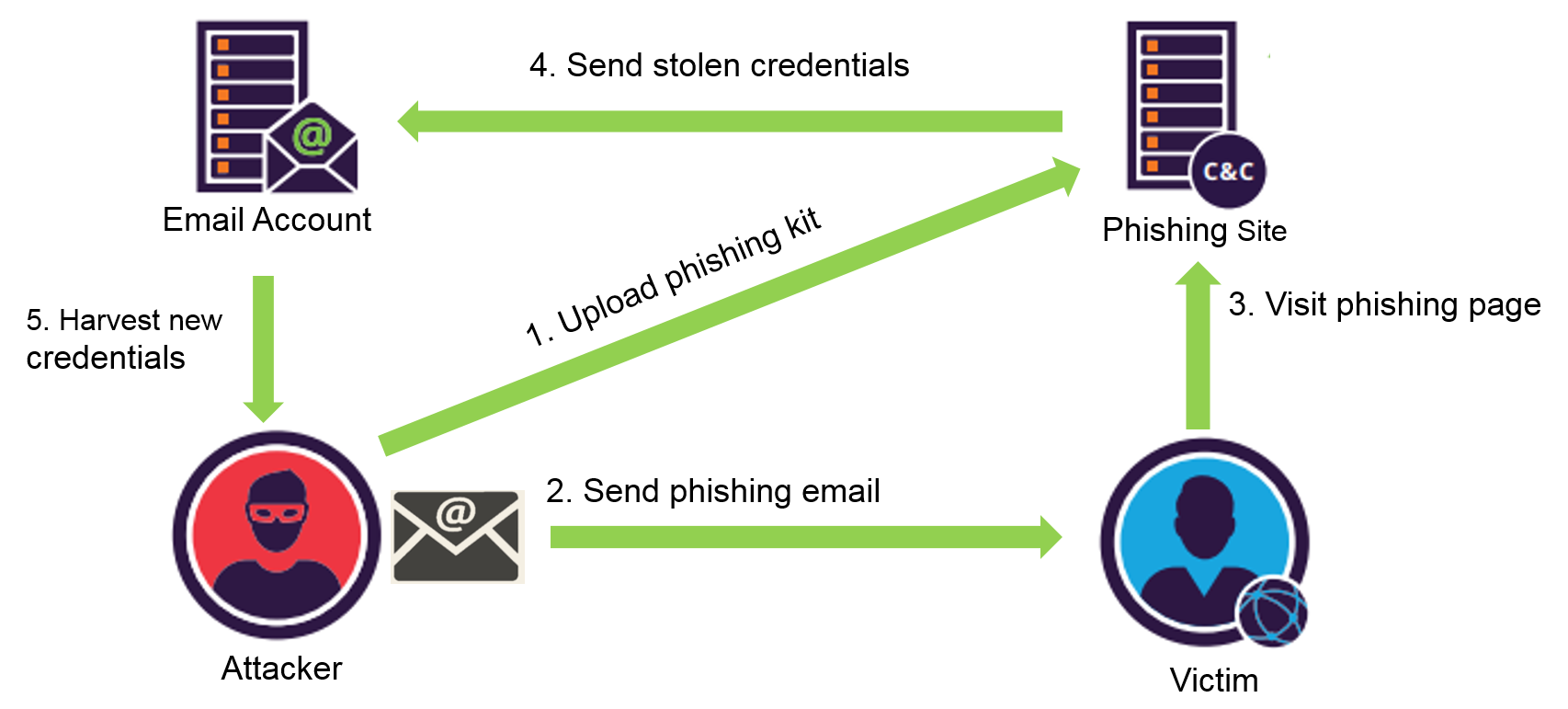
Anatomy Of A Phishing Attack Here’s how often some of the most common phishing techniques were deployed in 2023, according to a report by cloudflare inc. malicious link: 35.6%. identity deception: 14.2%. credential. Sms phishing, or smishing, is a mobile device oriented phishing attack that uses text messaging to convince victims to disclose account credentials or install malware. the victim is usually asked to click on a link, call a phone number or send an email. the attacker then asks the victim to provide private data. Phishing attacks are the practice of sending fraudulent communications that appear to come from a reputable source. it is usually done through email. the goal is to steal sensitive data like credit card and login information, or to install malware on the victim’s machine. phishing is a common type of cyber attack that everyone should learn. Phishing is a malicious technique based on deception, used to steal sensitive information (credit card data, usernames, and passwords, etc.) from users. the attackers pretend to be a trustworthy entity (usually by copying the look and feel of a big brand) to trick the victims into revealing their confidential data.
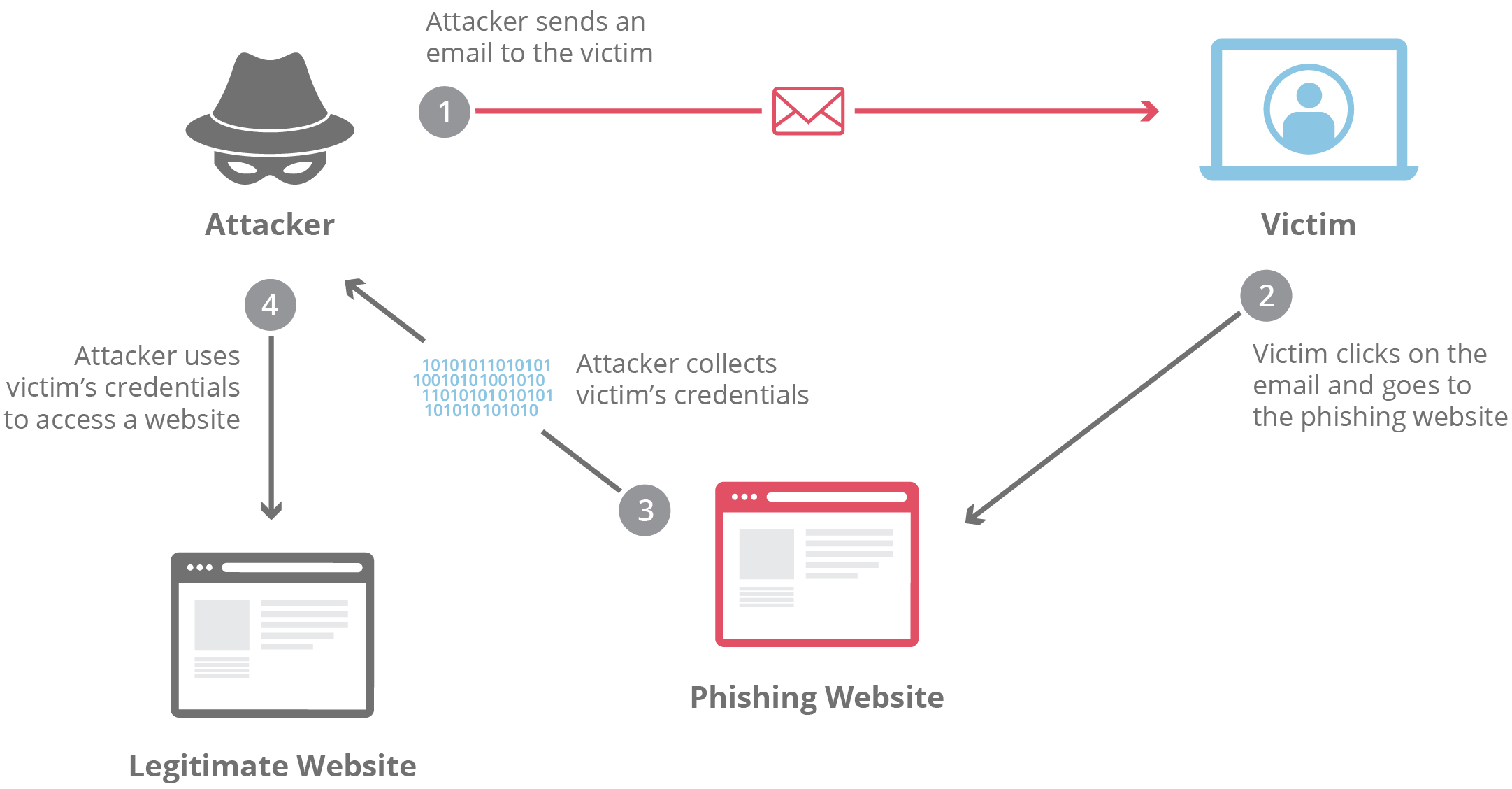
Phishing Attack Diagram Phishing attacks are the practice of sending fraudulent communications that appear to come from a reputable source. it is usually done through email. the goal is to steal sensitive data like credit card and login information, or to install malware on the victim’s machine. phishing is a common type of cyber attack that everyone should learn. Phishing is a malicious technique based on deception, used to steal sensitive information (credit card data, usernames, and passwords, etc.) from users. the attackers pretend to be a trustworthy entity (usually by copying the look and feel of a big brand) to trick the victims into revealing their confidential data. What is phishing? phishing is a type of cybersecurity attack during which malicious actors send messages pretending to be a trusted person or entity. phishing messages manipulate a user, causing them to perform actions like installing a malicious file, clicking a malicious link, or divulging sensitive information such as access credentials. Phishing attack. phishing is a form of social engineering in which a cyber threat actor poses as a trustworthy colleague, acquaintance, or organization to lure a victim into providing sensitive information or network access. the lures can come in the form of an email, text message, or even a phone call. if successful, this technique could.
What Is Phishing Attack Definition Types And How To Prevent It What is phishing? phishing is a type of cybersecurity attack during which malicious actors send messages pretending to be a trusted person or entity. phishing messages manipulate a user, causing them to perform actions like installing a malicious file, clicking a malicious link, or divulging sensitive information such as access credentials. Phishing attack. phishing is a form of social engineering in which a cyber threat actor poses as a trustworthy colleague, acquaintance, or organization to lure a victim into providing sensitive information or network access. the lures can come in the form of an email, text message, or even a phone call. if successful, this technique could.
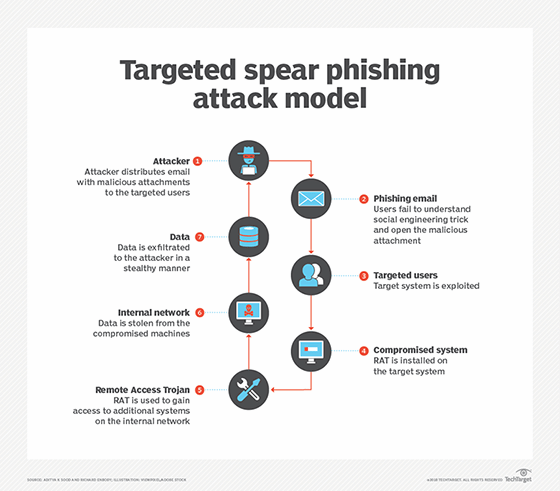
What Is Spear Phishing

Comments are closed.