How To Avoid Ransomware 9 Step Guide For 2024 Norton
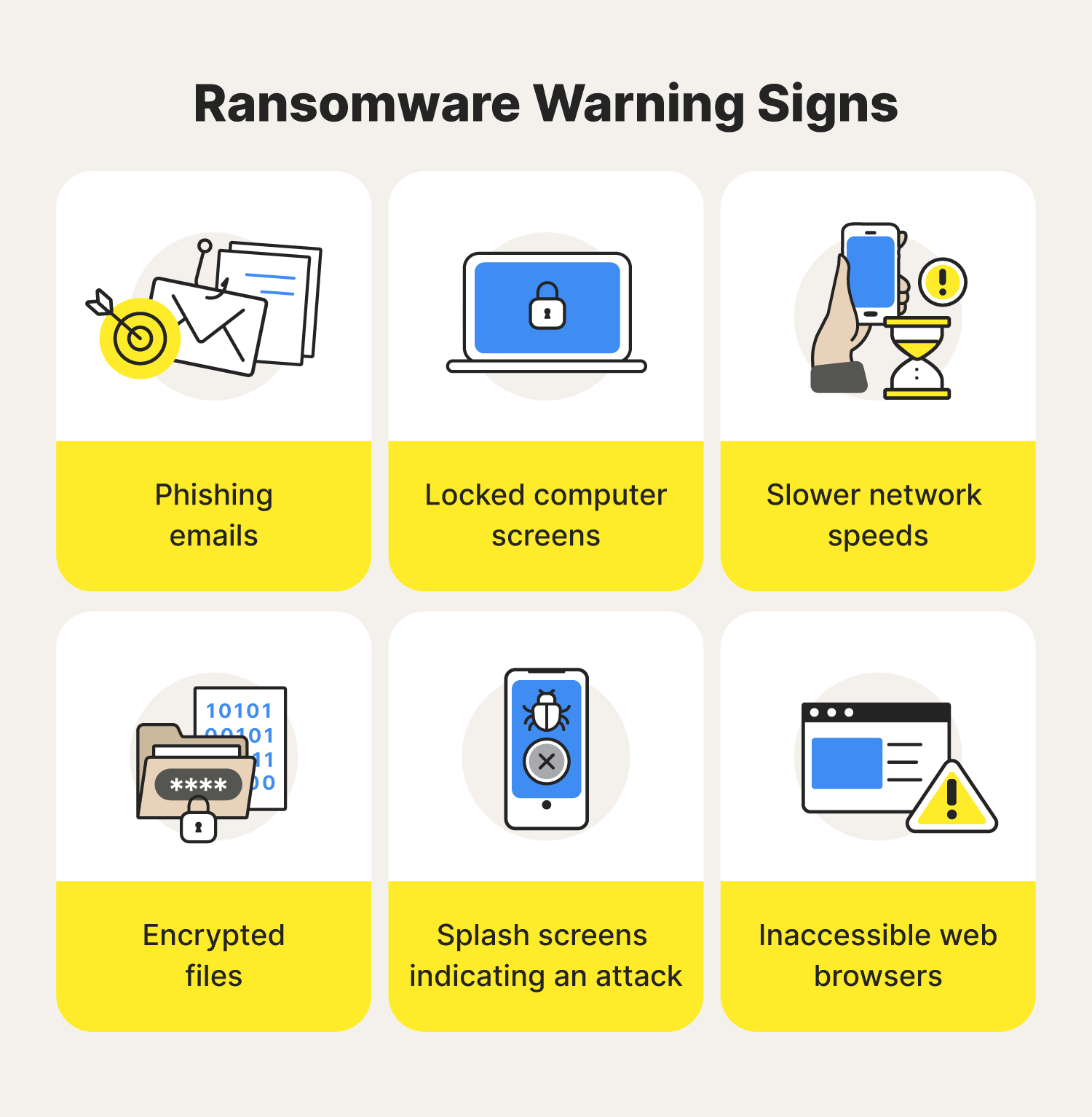
How To Avoid Ransomware 9 Step Guide For 2024 Norton Step 9: download antivirus software. in the same vein, downloading trusted antivirus software is also a great option for those learning how to combat ransomware. this software is capable of handling cyberthreats if they’re able to make it past your firewall. the round the clock protection antivirus software provides can:. New ransomware variants are constantly emerging, making it more important than ever to understand the dangers of these malicious programs. here are the top ransomware types hackers currently use. 1. crypto ransomware. systems affected: microsoft windows.
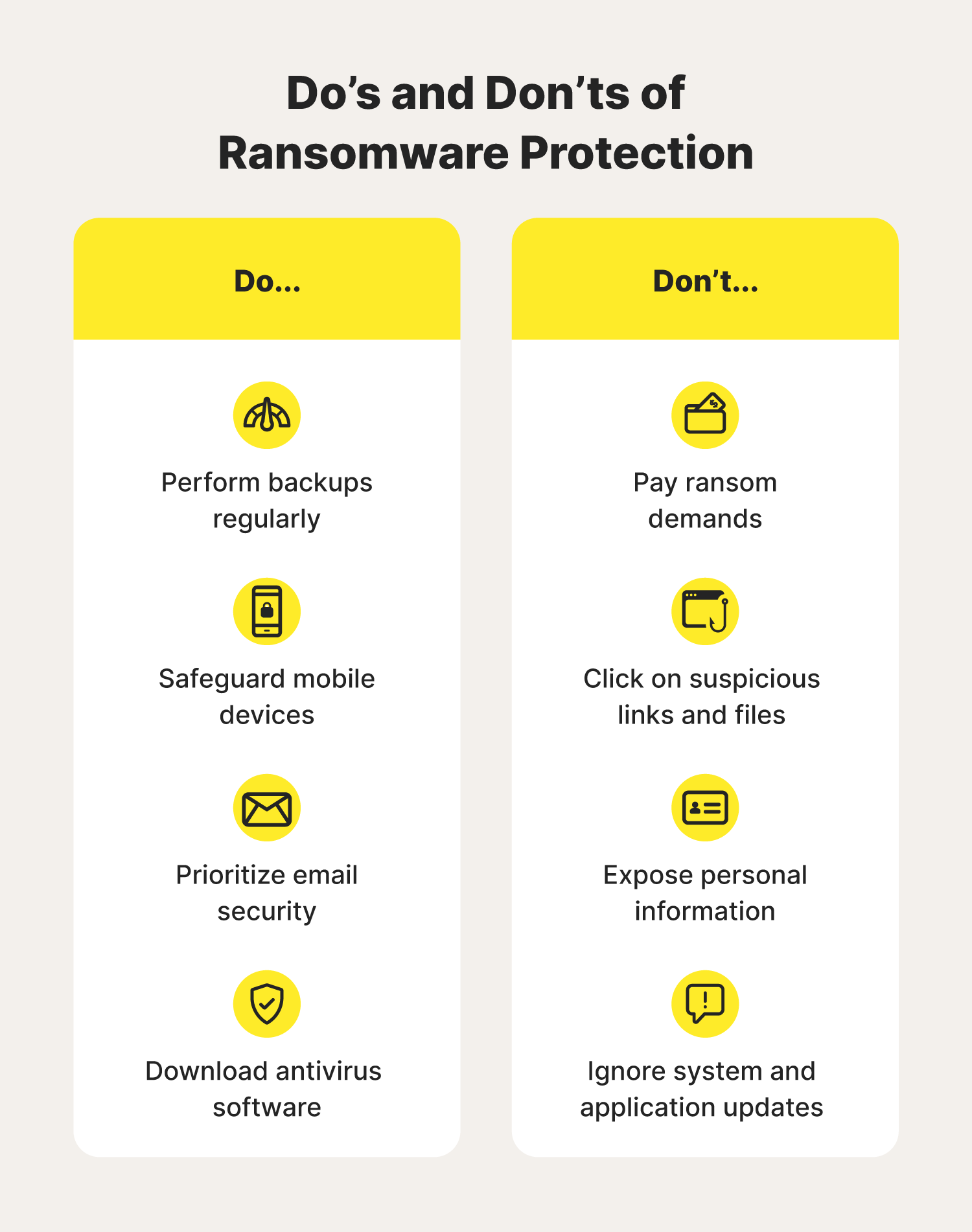
How To Avoid Ransomware 9 Step Guide For 2024 Norton By keeping an eye out for suspicious emails and texts, you can avoid losing your private information to a phishing scam. 6. change your passwords. it may seem like a simple step, but changing your passwords on a regular basis can go a long way to keeping scammers from accessing your online accounts. Best ransomware protection software in 2024. norton antivirus – the best overall software for comprehensive ransomware protection. bitdefender – the best for advanced ransomware protection with security suite integration. totalav – the best for strong ransomware protection with a free version. avira antivirus – the best for lightweight. Norton 360 keeps telling me to activate ransomware protection. if i click the button, it goes to backup settings which i don’t need. other than backup, does 360 have any ransomware protection that i need to enable?. Set up a firewall. a firewall is the first software based line of defense against ransomware. firewalls scan the incoming and outgoing traffic for potential risks, allowing the security team to monitor for signs of malicious payloads. to support your firewall activity, consider setting up: active tagging of workloads.

Comments are closed.