Hash Identifier Identify Hash Encryption Hash Cryptography

Implementation Principle Of Cryptographic Hash Algorithm Sobyte Identify and detect unknown hashes using this tool. this page will tell you what type of hash a given string is. if you want to attempt to decrypt them, click this link instead. decrypt hashes. hashes (max. 25 separated by newline, format 'hash [:salt]') include all possibilities (expert mode) submit & identify. hashes . A hash identifier is a tool that allows you to recognize the type of hash from a list of known hash functions. given an unknown hash, the identifier determines which hash function was likely used to generate it. there are hundreds of hashing algorithms, the majority return a hash as a number, usually stored in hexadecimal format.
Hash Function In Cryptography How Does It Work Infosec Insights Advanced commands for hash identifier: batch processing: hash identifier allows you to process multiple hashes at once using a text file. create a file, say hashes.txt, containing one hash per line, and then use the following command: hash id j r hashes.txt. the j flag enables batch processing, and r specifies the input file. The hash is the fingerprint result of the hash function, it identifies with a high probability the initial data without having to store it. this allows you to verify a password, without needing to know it. small changes in the input data lead to drastic changes in the resulting hash. this ensures data integrity and helps to check whether the. Namely, if you set a 40 character password and cannot successfully authenticate by typing only the first 39 characters, then this means that all characters are important, and this implies that this really is password hashing, not encryption (the stored value is used to verify a password, but the password cannot be recovered from the stored. About the hash analyzer. the aim of this online tool is to help identify a hash type. the tool can look at the characters that make up the hash to possibly identify which type of hash it is and what it may be used for. hash types this tool can positively identify: md5. sha1 (sha128).

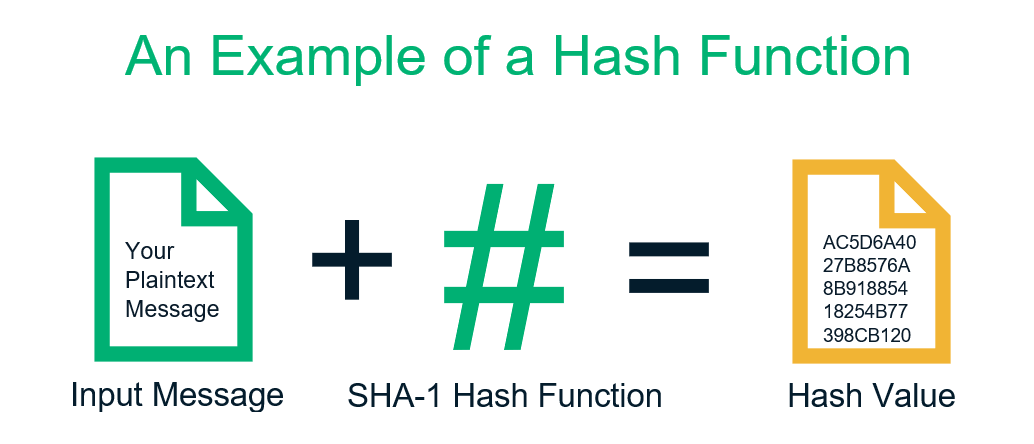
Cryptographic Hash Function Youtube Namely, if you set a 40 character password and cannot successfully authenticate by typing only the first 39 characters, then this means that all characters are important, and this implies that this really is password hashing, not encryption (the stored value is used to verify a password, but the password cannot be recovered from the stored. About the hash analyzer. the aim of this online tool is to help identify a hash type. the tool can look at the characters that make up the hash to possibly identify which type of hash it is and what it may be used for. hash types this tool can positively identify: md5. sha1 (sha128). Tools: hash identifier — quickly identify hash digest type. hash browser — browse latest generated hash digests. encoding playground — quickly encode decode strings using variety of non cryptographic encodings. random strings generator — generate from short to long random strings. reverse hash decoder, encoding, encryption, hashing, and. One purpose of a hash function in cryptography is to take a plaintext input and generate a hashed value output of a specific size in a way that can’t be reversed. but they do more than that from a 10,000 foot perspective. you see, hash functions tend to wear a few hats in the world of cryptography.
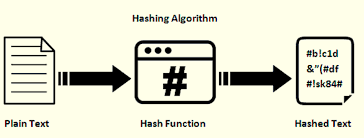
Hash Identification Using Machine Learning And 3 Tools вђ Jcharistech Tools: hash identifier — quickly identify hash digest type. hash browser — browse latest generated hash digests. encoding playground — quickly encode decode strings using variety of non cryptographic encodings. random strings generator — generate from short to long random strings. reverse hash decoder, encoding, encryption, hashing, and. One purpose of a hash function in cryptography is to take a plaintext input and generate a hashed value output of a specific size in a way that can’t be reversed. but they do more than that from a 10,000 foot perspective. you see, hash functions tend to wear a few hats in the world of cryptography.

Hash Identifier Identify Hash Encryption Hash Cryptography

Comments are closed.