Darkside Ransomware Decryption Tool
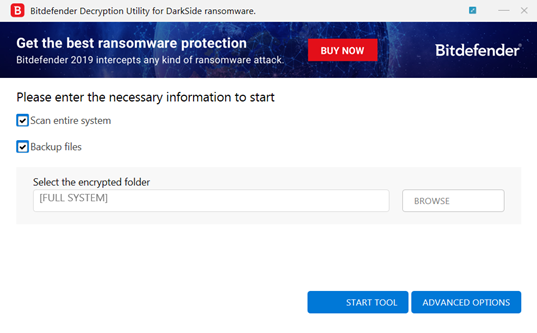
Darkside Ransomware Decryption Tool The Poortry/BurntCigar toolkit has added more ways for it to evade detection, evolved into something akin to a rootkit Defenders are being warned that a tool used by several ransomware gangs to Costs associated with ransomware incidents are on the rise, and even "zombie" malware operations like LockBit 30 continue to claim victims After dealing with a faulty decryption tool
Darkside Ransomware Decryption Tool FBI Deputy Director Paul Abbate described DarkSide, the alleged authors of the ransomware that was used in the attack, as a “Russia-based cybercrime group,” offering no evidence for the claim ESET researchers examine the recent activities of the CosmicBeetle threat actor, documentingt its new ScRansom ransomware and highlighting connections to other well-established ransomware gangs Using publicly available reports, K12 SIX identified at least 325 ransomware attacks on school districts across the United States between April 2016 and the end of November 2022 From January 2023 It was the first known case of native English-speaking hackers in the United States and Britain teaming up with ransomware gangs based in Russia But that made-for-Hollywood narrative has eclipsed
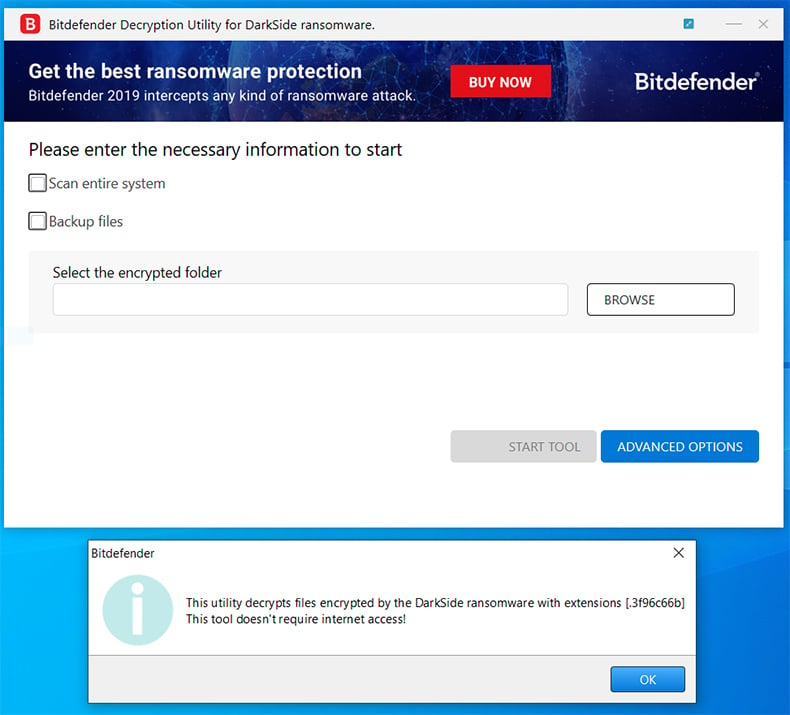
Darkside Ransomware Decryption Removal And Lost Files Recovery Using publicly available reports, K12 SIX identified at least 325 ransomware attacks on school districts across the United States between April 2016 and the end of November 2022 From January 2023 It was the first known case of native English-speaking hackers in the United States and Britain teaming up with ransomware gangs based in Russia But that made-for-Hollywood narrative has eclipsed Once inside, a ransomware program locks up user files through encryption This preserves the data but makes it unreadable and inaccessible to anyone without a decryption key At this point Although ransomware is not only a long-established between the attacker and the victim before the unsolicited remote tool, in this case the aforementioned Anydesk, access request was sent With a well-made weeding tool and some vigilance, banishing these pesky plants can be fairly simple Weeds proliferate seemingly overnight, and it’s easiest to remove them when they’re young No workbench is complete without at least one good rotary tool These amazing devices are capable of drilling, sanding, cutting, glassworking, grinding, carving, and even cleaning With the right
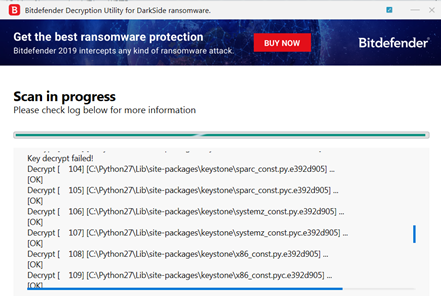
Darkside Ransomware Decryption Tool Once inside, a ransomware program locks up user files through encryption This preserves the data but makes it unreadable and inaccessible to anyone without a decryption key At this point Although ransomware is not only a long-established between the attacker and the victim before the unsolicited remote tool, in this case the aforementioned Anydesk, access request was sent With a well-made weeding tool and some vigilance, banishing these pesky plants can be fairly simple Weeds proliferate seemingly overnight, and it’s easiest to remove them when they’re young No workbench is complete without at least one good rotary tool These amazing devices are capable of drilling, sanding, cutting, glassworking, grinding, carving, and even cleaning With the right

Comments are closed.