Cyber Kill Chain Model
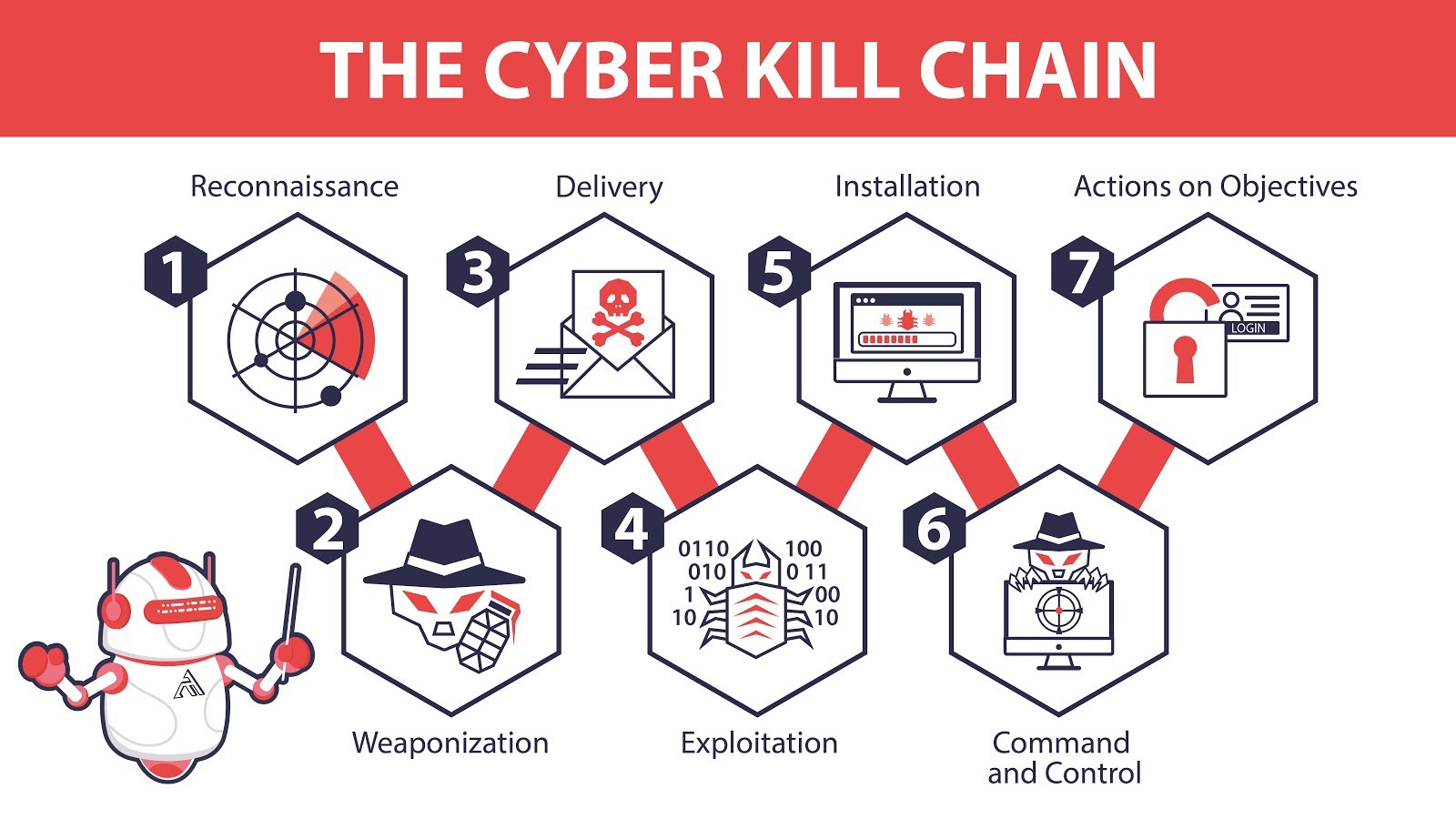
An Introduction To Mitre Att Ck вђ Cybots Ai Cybersecurity Learn how lockheed martin's cyber kill chain® framework helps identify and prevent cyber intrusions. explore the seven steps of the model, download guides and white papers, and watch videos from cyber experts. Learn how attackers use the cyber kill chain framework to infiltrate and exploit networks, and how to prevent or respond to cyber threats. the article explains each stage of the cyber kill chain with examples and references.
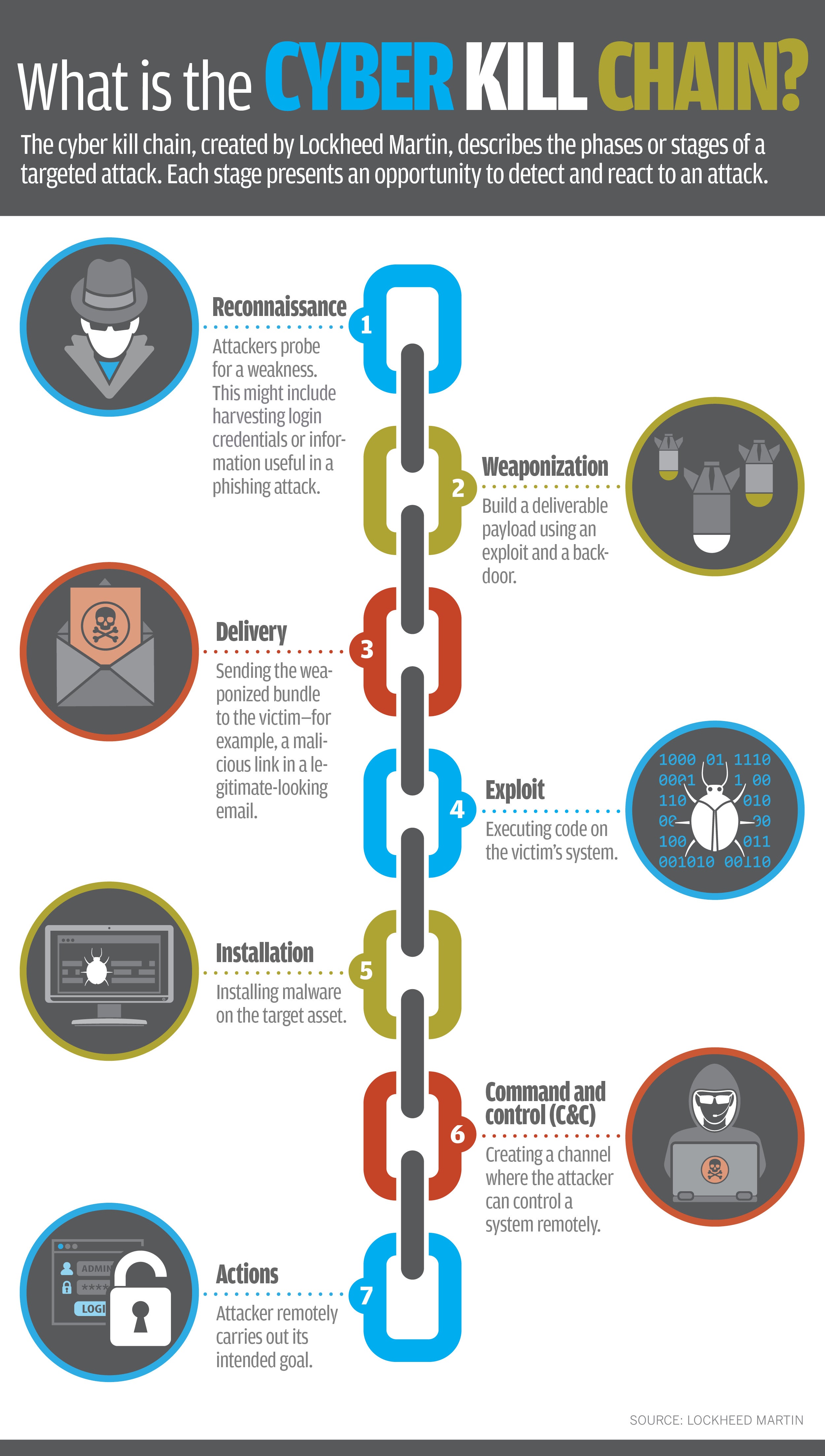
What Is The Cyber Kill Chain A Model For Tracing Cyberattacks Cso Online Learn what the cyber kill chain is, a framework that outlines the stages of common cyberattacks and how to prevent or detect them. also, explore the evolution, limitations and challenges of the cyber kill chain model. A cyber kill chain is a security framework designed to identify and stop sophisticated cyberattacks by breaking down the attack into multiple stages. this model helps security teams recognize, intercept, or prevent attacks before they impact an organization. the concept of a kill chain originated from military operations, where an enemy attack. The cyber kill chain is the step by step techniques that identify, detects, and stops the vulnerable activity. it starts with the phase of reconnaissance and each phase represents the activities of cyber attacks. organizations use various security tools to identify and detect these attacks. here are the phases that represent the working of the. In cybersecurity, the cyber kill chain is a model outlining the various phases of common cyberattacks. using the cyber kill chain, organizations can trace the stages of a cyberattack to better anticipate and prevent against cyber threats in the future. each stage of the cyber kill chain is related to a specific type of activity in a cyberattack.

Kill Chain Cyberhoot Cyber Library The cyber kill chain is the step by step techniques that identify, detects, and stops the vulnerable activity. it starts with the phase of reconnaissance and each phase represents the activities of cyber attacks. organizations use various security tools to identify and detect these attacks. here are the phases that represent the working of the. In cybersecurity, the cyber kill chain is a model outlining the various phases of common cyberattacks. using the cyber kill chain, organizations can trace the stages of a cyberattack to better anticipate and prevent against cyber threats in the future. each stage of the cyber kill chain is related to a specific type of activity in a cyberattack. Learn what the cyber kill chain model is, how it was developed, and what are its seven stages: reconnaissance, weaponization, delivery, exploitation, installation, command and control, and actions on objectives. see how this model can help you detect and stop cyberattacks at different stages. The cyber kill chain, also known as the cyberattack lifecycle, is a model developed by lockheed martin that describes the phases of a targeted cyberattack. it breaks down each stage of a malware.
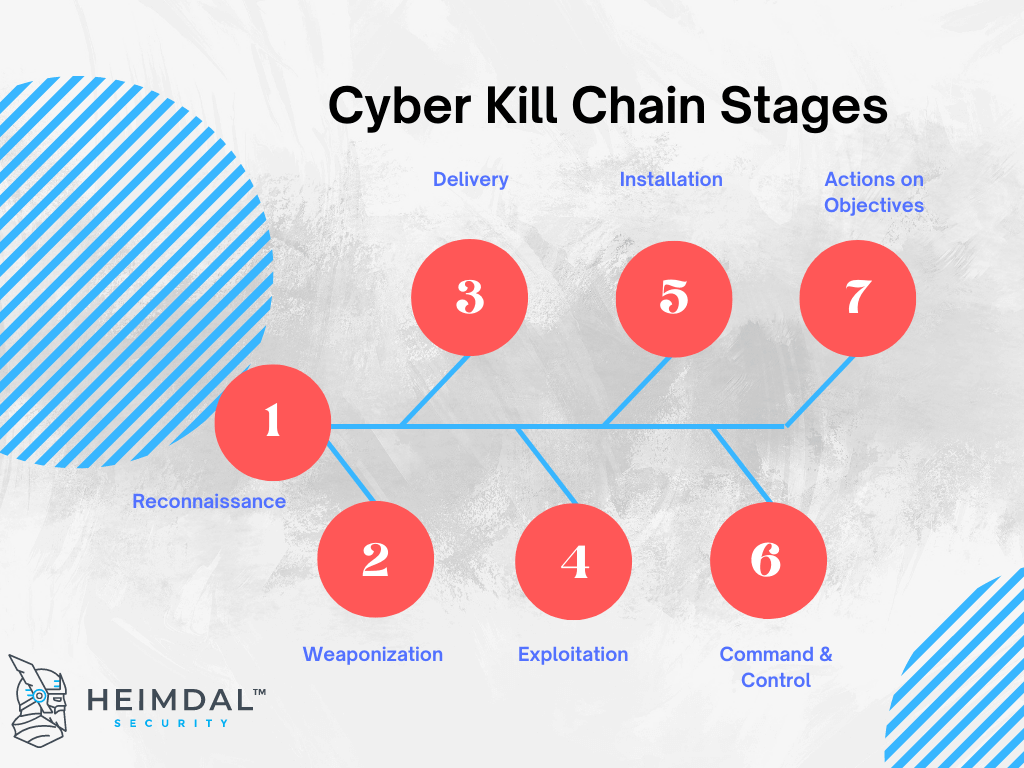
The Cyber Kill Chain Ckc Explained Learn what the cyber kill chain model is, how it was developed, and what are its seven stages: reconnaissance, weaponization, delivery, exploitation, installation, command and control, and actions on objectives. see how this model can help you detect and stop cyberattacks at different stages. The cyber kill chain, also known as the cyberattack lifecycle, is a model developed by lockheed martin that describes the phases of a targeted cyberattack. it breaks down each stage of a malware.
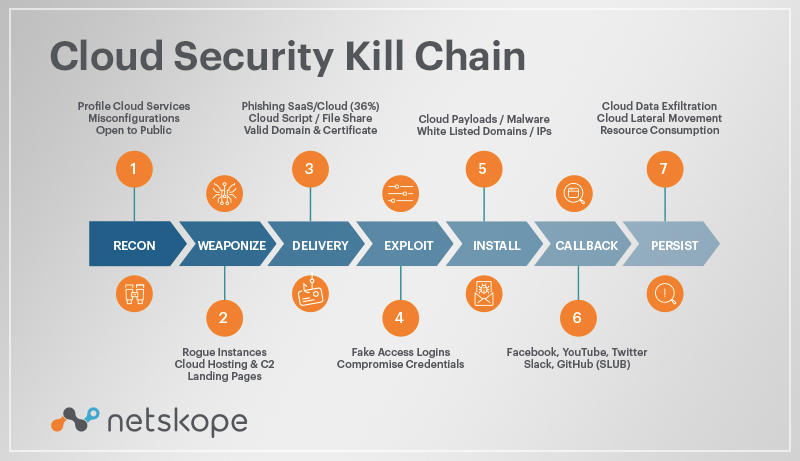
What Is A Cyber Security Kill Chain Netskope

Comments are closed.