Asymmetric Encryption What It Is Why Your Security Depends On It

Asymmetric Encryption What It Is Why Your Security Depends On It Website security: asymmetric encryption is used as part of the ssl tls handshake. the handshake is the virtually instantaneous process in which a server authenticates to the browser that tries to connect with it. the two parties exchange data they can use for key exchange or generation. As the name implies, asymmetric encryption is different on each side; the sender and the recipient use two different keys. asymmetric encryption, also known as public key encryption, uses a public key private key pairing: data encrypted with the public key can only be decrypted with the private key. tls (or ssl), the protocol that makes https.

Asymmetric Encryption What It Is Why Your Security Depends On It Asymmetric encryption keeps data secure by using cryptographic algorithms to generate a pair of keys: a public key and a private key. anyone can use the public key to encrypt data, but only those with the right private key can decrypt that data to read it. keys function like complex codes needed to unlock a safe. The advanced encryption standard (aes) is a secure form of symmetric encryption that divides data into blocks of 128 bits, then uses 14 rounds of encryption to scramble them beyond recognition. aes has been widely adopted for secure applications, including cloud security, hard drive encryption, and electronic payments. The aim of asymmetric key encryption is to provide a method for securely encrypting data across public channels, in addition to authentication and data integrity. there is no key distribution issue, as there would be with symmetric encryption, because the exchange of keys is not necessary. 2. keys for asymmetric encryption are large. Asymmetric cryptography involves a pair of keys to encrypt and decrypt data. the two participants in the asymmetric encryption workflow are the sender and the receiver. each has its own pair of public and private keys. first, the sender obtains the receiver's public key. next, the plaintext message is encrypted by the sender using the receiver.

What Is Asymmetric Encryption How Does It Work Infosec Insights The aim of asymmetric key encryption is to provide a method for securely encrypting data across public channels, in addition to authentication and data integrity. there is no key distribution issue, as there would be with symmetric encryption, because the exchange of keys is not necessary. 2. keys for asymmetric encryption are large. Asymmetric cryptography involves a pair of keys to encrypt and decrypt data. the two participants in the asymmetric encryption workflow are the sender and the receiver. each has its own pair of public and private keys. first, the sender obtains the receiver's public key. next, the plaintext message is encrypted by the sender using the receiver. Asymmetric encryption (also known as asymmetric cryptography) allows users to encrypt information using shared keys. you need to send a message across the internet, but you don't want anyone but the intended recipient to see what you've written. asymmetric encryption can help you achieve that goal. asymmetric cryptography techniques allow for. Asymmetric encryption (also known as asymmetric cryptography) is public key encryption. here, the algorithm carries out encryption and decryption with the help of two pairs of keys: public key: the public key helps in message encryption. private key: the private key helps in message decryption. the private key is also known as the secret key as.
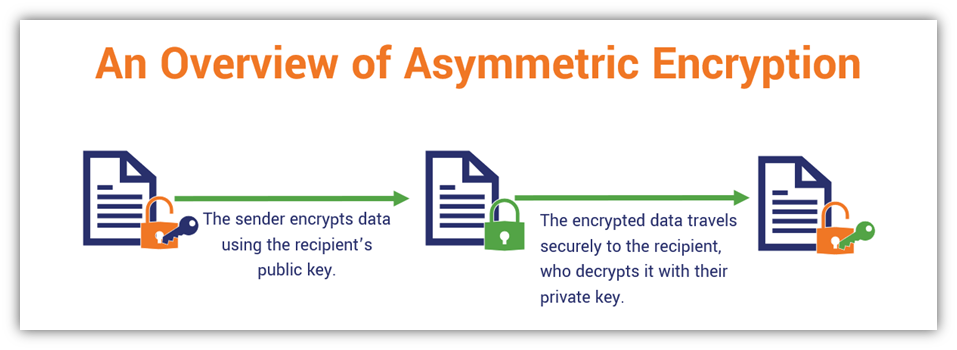
Asymmetric Encryption What It Is Why Your Security Depends On It Asymmetric encryption (also known as asymmetric cryptography) allows users to encrypt information using shared keys. you need to send a message across the internet, but you don't want anyone but the intended recipient to see what you've written. asymmetric encryption can help you achieve that goal. asymmetric cryptography techniques allow for. Asymmetric encryption (also known as asymmetric cryptography) is public key encryption. here, the algorithm carries out encryption and decryption with the help of two pairs of keys: public key: the public key helps in message encryption. private key: the private key helps in message decryption. the private key is also known as the secret key as.

Comments are closed.