An Introduction To Owasp Top 10 Vulnerabilities Broken Access Control

Owasp Top 10 Broken Access Control вђ Raxis Moving up from the fifth position, 94% of applications were tested for some form of broken access control with the average incidence rate of 3.81%, and has the most occurrences in the contributed dataset with over 318k. notable common weakness enumerations (cwes) included are cwe 200: exposure of sensitive information to an unauthorized actor. Access control is only effective in trusted server side code or server less api, where the attacker cannot modify the access control check or metadata. except for public resources, deny by default. implement access control mechanisms once and re use them throughout the application, including minimizing cross origin resource sharing (cors) usage.

What Are The Owasp Top 10 Vulnerabilities And How To Mitigate Them Owasp top 10 broken access control is a category of security vulnerabilities that allows attackers to gain unauthorized access to resources or perform unauthorized actions such as accessing sensitive data, modifying data, or disrupting the application. there are many different ways that broken access control can occur. Explore some real world scenarios of broken access control. open in app broken access control guide: introduction; team to learn more about owasp and owasp top 10 security vulnerabilities:. Description. access control, sometimes called authorization, is how a web application grants access to content and functions to some users and not others. these checks are performed after authentication, and govern what ‘authorized’ users are allowed to do. access control sounds like a simple problem but is insidiously difficult to. In cybersecurity, the owasp top 10 is an invaluable resource for ensuring that web applications are secure. the list changes annually depending on what vulnerabilities become more prevalent. for me, one of the most interesting things about this year’s version is that broken access control vulnerabilities jumped from no. 5 in 2020 to no.1.

An Introduction To Owasp Top 10 Vulnerabilities Broken Access Control Description. access control, sometimes called authorization, is how a web application grants access to content and functions to some users and not others. these checks are performed after authentication, and govern what ‘authorized’ users are allowed to do. access control sounds like a simple problem but is insidiously difficult to. In cybersecurity, the owasp top 10 is an invaluable resource for ensuring that web applications are secure. the list changes annually depending on what vulnerabilities become more prevalent. for me, one of the most interesting things about this year’s version is that broken access control vulnerabilities jumped from no. 5 in 2020 to no.1. Scenario #2: an attacker simply force browses to target urls. admin rights are required for access to the admin page. if an unauthenticated user can access either page, it’s a flaw. if a non admin can access the admin page, this is a flaw. a5:2017 broken access control on the main website for the owasp foundation. Publishedapril 29, 2022. broken access controls are the most common vulnerability discovered during web application penetration testing. it moved up from 5th position to the 1st position in the 2021 owasp top 10 web application vulnerabilities list. access control vulnerabilities occur when users are able to act outside of their intended.

Day 3 Owasp Top 10 2021 вђ 1 Broken Access Control Scenario #2: an attacker simply force browses to target urls. admin rights are required for access to the admin page. if an unauthenticated user can access either page, it’s a flaw. if a non admin can access the admin page, this is a flaw. a5:2017 broken access control on the main website for the owasp foundation. Publishedapril 29, 2022. broken access controls are the most common vulnerability discovered during web application penetration testing. it moved up from 5th position to the 1st position in the 2021 owasp top 10 web application vulnerabilities list. access control vulnerabilities occur when users are able to act outside of their intended.
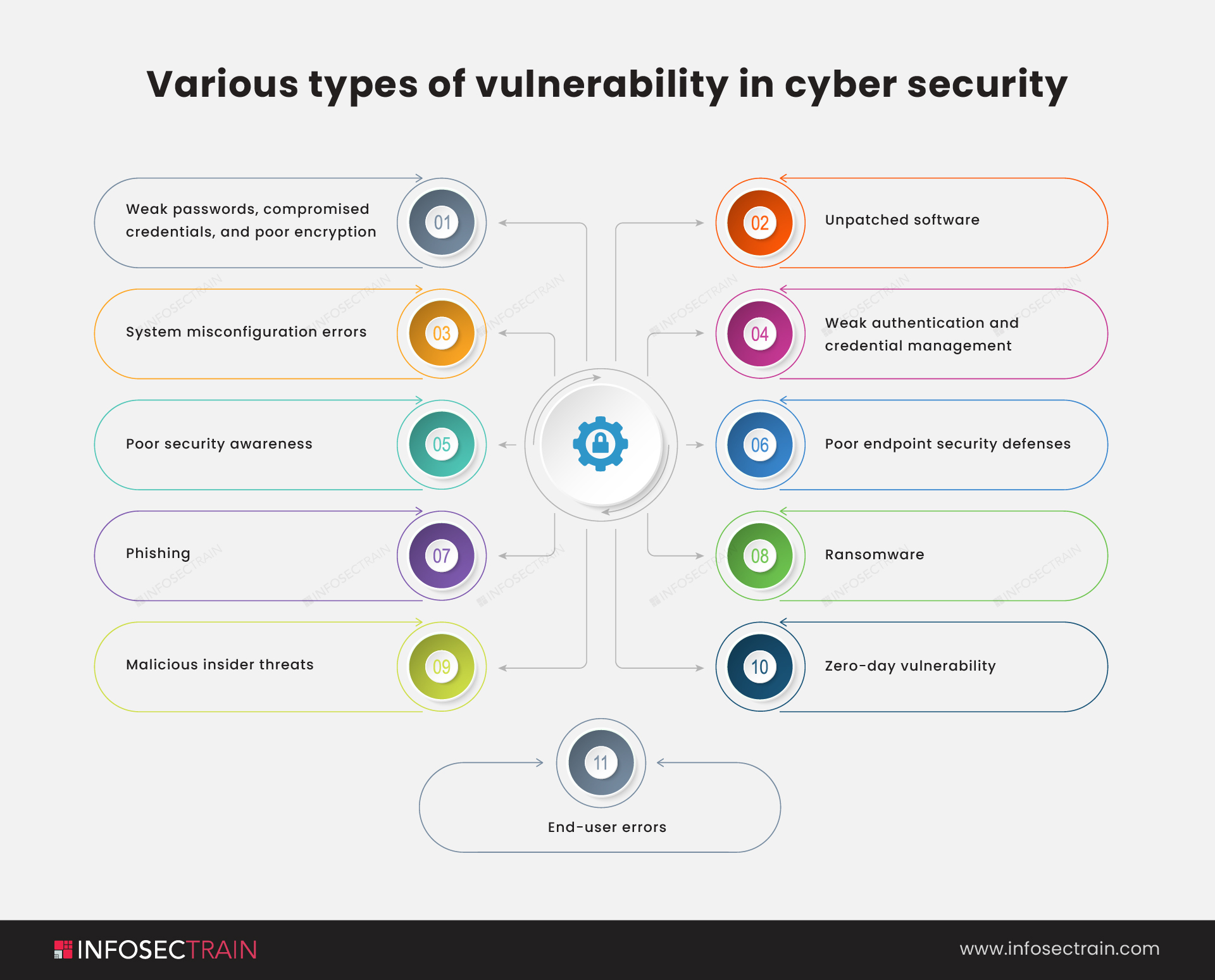
Owasp Top 10 Vulnerabilities 2021 Revealed Infosectrain

Comments are closed.